Become a leader in the IoT community!
Join our community of embedded and IoT practitioners to contribute experience, learn new skills and collaborate with other developers with complementary skillsets.
Hey guys please I’m encountering a challenge with my Azure IoT Hub configuration. I need to allow incoming traffic from IoT devices through public endpoints, but I’m struggling to restrict […]
Hi everyone, I’m working on an IoT project that involves storing data in a database. While writing the SQL code, I encountered the following error: “violated – parent key not […]
How can we strike a balance between security and performance in IoT devices, especially low-power ones, to ensure robust protection without compromising efficiency, potentially through the use of lightweight encryption […]
Forums are designed to help DevHeads community members come to quick resolution on a variety of systems integration topics. These differ from the #seeking-collabs (find a professional dev who can […]
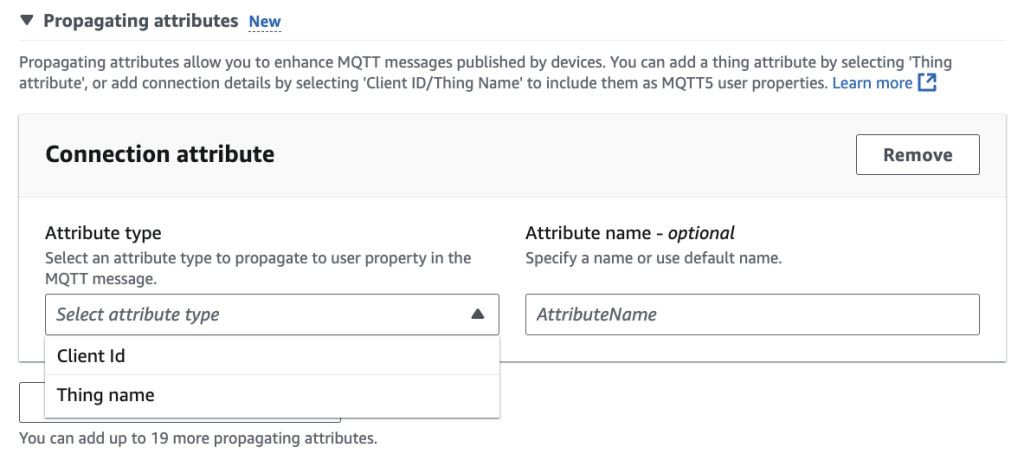
AWS added propagating attributes – contextual metadata from thing attributes or connection details. What does it mean? Previously, we had to configure and deploy IoT Rule to extract the `Client […]
Julius Caesar protected his confidential information by encrypting it using a cipher. Caesar’s cipher shifts each letter by a number of letters. If the shift takes you past the end […]
Hello #edge-networking am developing a smart automation system for factory The system needs to collect large data from sensors ( temperature, humidity, motion, door/window status) and control actuators (lights, thermostats, […]
Hi all! When designing an Arduino-based embedded system, how can secure firmware updates be ensured to prevent unauthorized modifications or potential exploits? Discuss methods for securely updating firmware on Arduino […]

In my recent experience with AWS, I encountered an unusual situation where access to the Lambda service was restricted due to an identified security violation. It’s a reminder that while […]