Become a leader in the IoT community!
Join our community of embedded and IoT practitioners to contribute experience, learn new skills and collaborate with other developers with complementary skillsets.
In this video, I discuss using a Private Key in the MQTT connection setup. It’s crucial to keep the Private Key confidential and not share it with any third party. […]
To increase the IoT domain’s security posture, I decided to offer 100 free coupons for my Udemy training. After taking this training, you will: ✅ Understand how AWS IoT Core […]
AWS IoT Greengrass is an open-source Internet of Things (IoT) edge runtime and cloud service for IoT applications. It is my (un)favorite IoT service. Pros: Runs on edge devices. Communicates […]
I’m developing an IoT device using SIM7080G cellular chip and ESP32-C3. With the rise of IoT attacks and vulnerabilities, I want to ensure my device is fortified against unauthorized access, […]
Hi guys @IoT Cloud I plan on making a solution where devices need to communicate with multiple endpoints, including an API for non-telemetry data. To avoid additional authentication methods, I’m […]
Hey guys please I’m encountering a challenge with my Azure IoT Hub configuration. I need to allow incoming traffic from IoT devices through public endpoints, but I’m struggling to restrict […]
Forums are designed to help DevHeads community members come to quick resolution on a variety of systems integration topics. These differ from the #seeking-collabs (find a professional dev who can […]
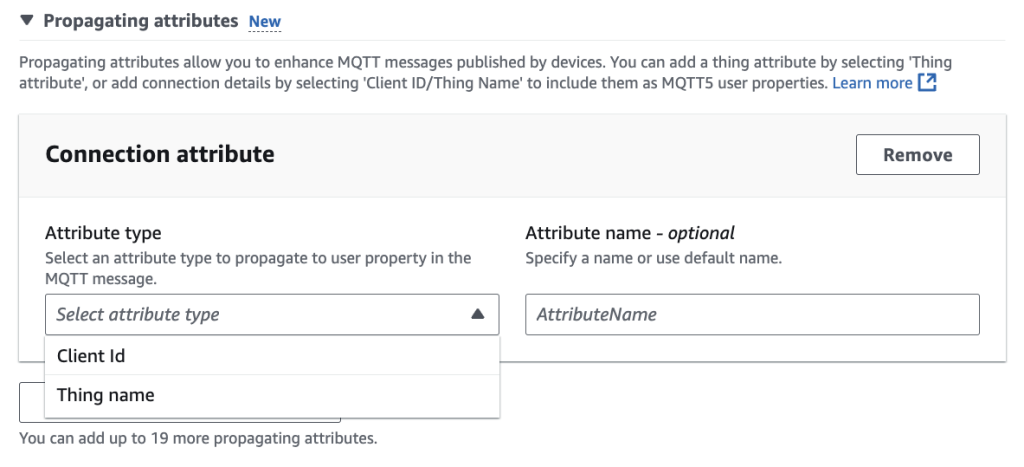
AWS added propagating attributes – contextual metadata from thing attributes or connection details. What does it mean? Previously, we had to configure and deploy IoT Rule to extract the `Client […]
Hey guys @Middleware & OS I want to learn about using TPM in embedded Linux on ARM for secure boot, TrustZone, etc. I’m struggling to find up-to-date resources. Most of […]