Become a leader in the IoT community!
Join our community of embedded and IoT practitioners to contribute experience, learn new skills and collaborate with other developers with complementary skillsets.
Julius Caesar protected his confidential information by encrypting it using a cipher. Caesar’s cipher shifts each letter by a number of letters. If the shift takes you past the end […]
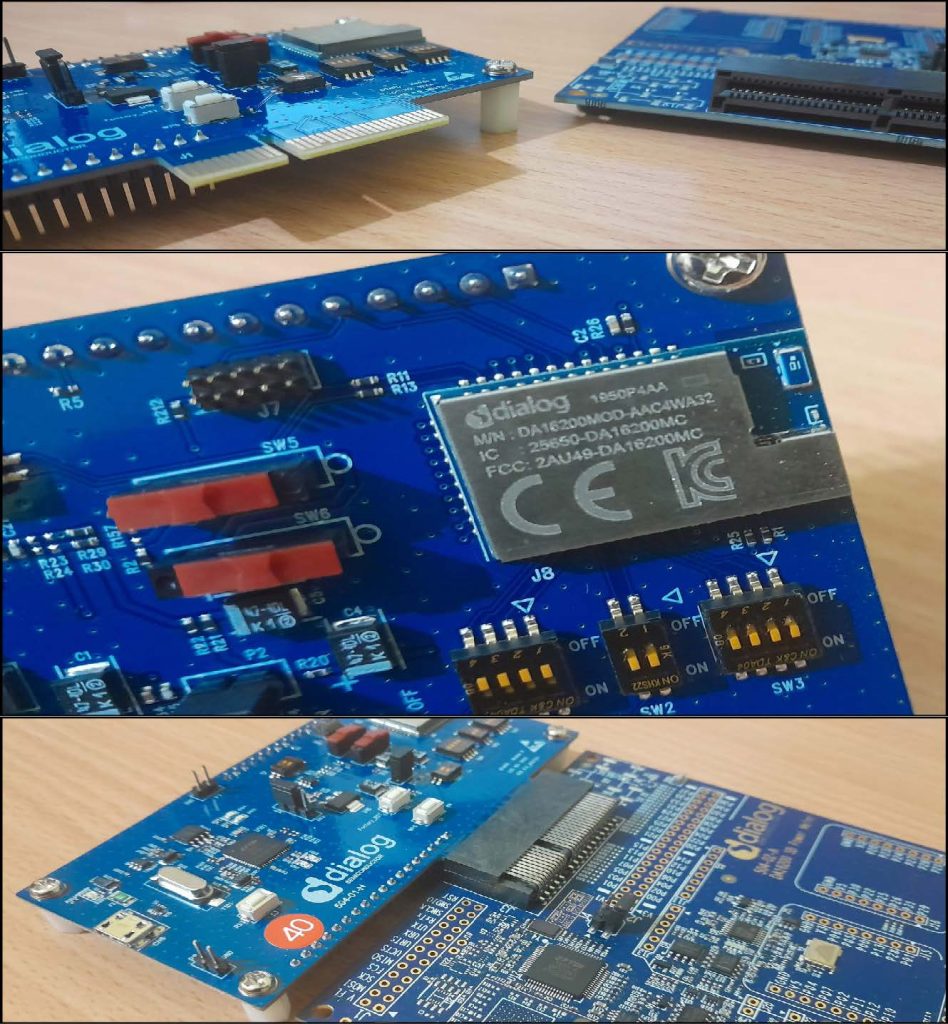
* *Reviewer:* @ngu25 * *Full Review and Getting Started Guide:* https://www.devheads.io/wp-content/uploads/2024/04/DA16200MOD-DEVKT-P_DevHeads_Review.pdf The DA16200MOD-DEVKT-P is an ultra-low-power Wi-Fi module development kit based on the DA16200MOD and DA16200 Wi-Fi system-on-chip (SoC). It’s […]
Hello #edge-networking am developing a smart automation system for factory The system needs to collect large data from sensors ( temperature, humidity, motion, door/window status) and control actuators (lights, thermostats, […]
Hi all! When designing an Arduino-based embedded system, how can secure firmware updates be ensured to prevent unauthorized modifications or potential exploits? Discuss methods for securely updating firmware on Arduino […]

In my recent experience with AWS, I encountered an unusual situation where access to the Lambda service was restricted due to an identified security violation. It’s a reminder that while […]
In this video, I discuss using a Private Key in the MQTT connection setup. It’s crucial to keep the Private Key confidential and not share it with any third party. […]
To increase the IoT domain’s security posture, I decided to offer 100 free coupons for my Udemy training. After taking this training, you will: ✅ Understand how AWS IoT Core […]
I’m developing an IoT device using SIM7080G cellular chip and ESP32-C3. With the rise of IoT attacks and vulnerabilities, I want to ensure my device is fortified against unauthorized access, […]
Hi guys @IoT Cloud I plan on making a solution where devices need to communicate with multiple endpoints, including an API for non-telemetry data. To avoid additional authentication methods, I’m […]